Information, LatestNews, Uncategorized
AVTECH CCTV System Maleware Infection
AVTECH CCTV Equipment user, do the following immediately.
- Unplugged your AVTECH DVR/NVR/IP Cameras from the internet.
- Check on AVTECH website (http://www.avtech.com.tw) if upgraded firmware is available.
- Download and upgrade the firmware to your CCTV Equipment
For older AVTECH equipment, it’s unlikely that AVTECH will release any firmware patches. If you don’t see your equipment listed (http://211.75.84.102/e_news/Security/Security.html) , most likely it’ll not have any firmware upgrade.
If there is no firmware upgrade for your AVTECH model, it’s recommended that you take your AVTECH Equipment offline or replace them with another brand/model that has the security flaw fixed.
If you wish to do the firmware upgrade yourself, here’s how to do it.
Here’s some symptom that you might face if your system is infected. Not all infected system will exhibit symptoms.
- Slow down of your network
- Unable to login to your AVTECH CCTV System
- Restarting of AVTECH CCTV system works only temporary.
What the malware will do
“The points of entry for this new Linux malware are connected AVTech devices such as IP cameras, CCTV equipment, and network recorders that support the AVTech cloud. Once the malware is installed onto the device, it gathers system information and network activity data. It can also execute shell commands from the malicious actor, initiate Distributed Denial of Service (DDoS) attacks, and terminate itself,” the researchers explain.
The attacker will have full control of your system and will be able to monitor data in your network. It might allow them to copy files from insecure file servers in your network as well.
A new malware that targets Linux-based Internet of Things (IoT) devices has been detected by Search-Lab, a Security research and development firm. This Linux ARM malware called as ELF_IMEIJ.A exploits a vulnerability in devices from AVTech, a surveillance technology company.
As an AVTech user, you can do the following to protect your device,
- Change the default admin password (All our Devices are installed with the default password changed)
- Never expose the web interface of any Avtech device to the internet (Disable Remote Viewing through Internet)
Ref :-
http://news.thewindowsclub.com/new-linux-malware-attacks-avtech-iot-devices-88739/
http://www.securityweek.com/ddos-malware-targets-avtech-cgi-vulnerability
http://blog.trendmicro.com/trendlabs-security-intelligence/new-linux-malware-exploits-cgi-vulnerability/
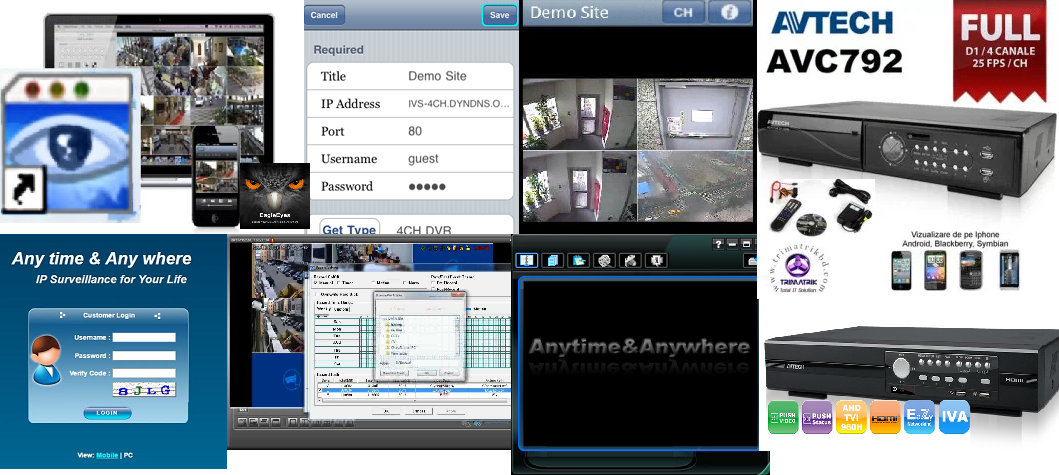
Here’s how AVTECH System looks like. If you are using any of the software/dvr that look like this, then most likely you are using AVTECH equipment.
Updates 2017 March 24
It appear that major ISP from Singapore had taken steps to block the spread of the malware ELF_IMEIJ on AVTECH CCTV System through their network as of 24 March 2017 by blocking certain ways the malware spread.
However, there’s no easy way to determine if your system is infected with the Malware as not all infected system will exhibit any symptoms. Your CCTV System may appear to be functioning normally but the attacker will have full control of your system and will be able to monitor data in your network. It may allow them to copy files from file servers, hacked or infect other devices/computer in your network as well. (Read more)
Only way is to reload the firmware to the AVTECH DVR/NVR. For those without upgraded firmware, there’s no guarantee that reloading the firmware will prevent re-infection as any infected devices connected will lead to reinfection.
As Lakson no longer have any customers with AVTECH equipment under warranty/maintenance/subscriptions, support for AVTECH system will ceased as there’s no easy method to detect or prevent reinfection for devices without upgraded firmware.
Our recommended is to immediately upgrade those models with firmware updates from AVTECH immediately and replace those without any firmware updates immediately.

